frida小总结(1)
终于要更新博客了,有点幽默了……
最近碰到了一个神奇的题目,记录一下感想
首先,我本来都是习惯用jeb分析apk的,但是后来听不记得哪位师傅说,其实jadx反编译更贴近源代码,而且我发现,原来jadx也是可以完成apk java层动态调试工作的,所以成功转手
我们可以看一下大致的代码逻辑
1 | //Mainactivity |
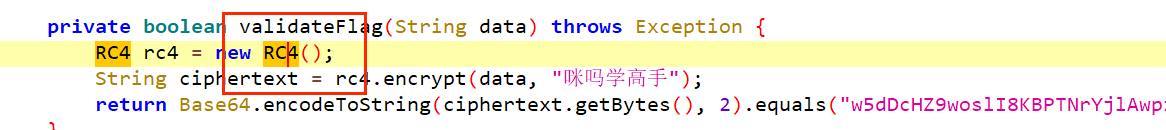
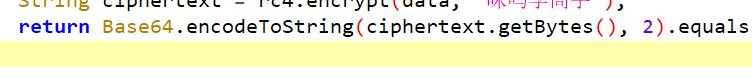
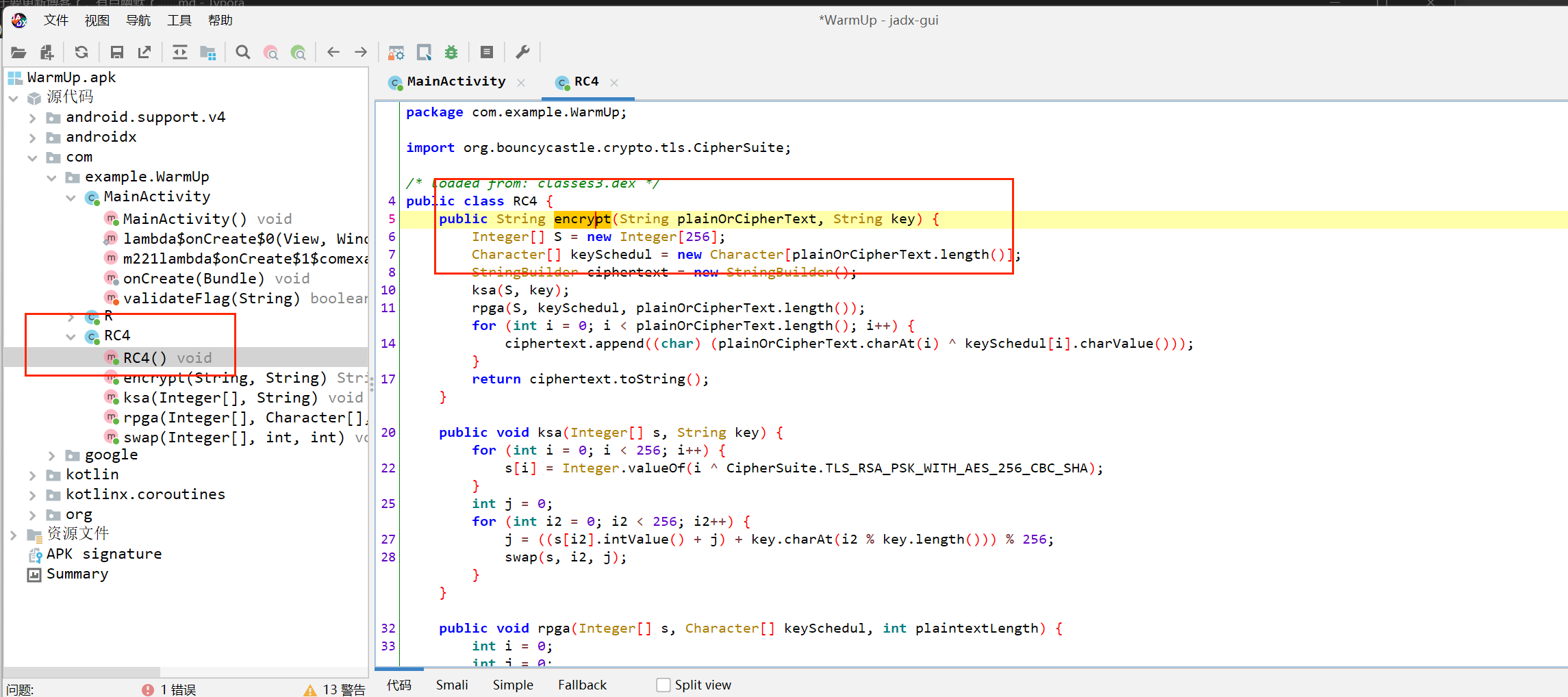
题目不难,简单分析就知道是RC4魔改+base64了,
再看一下RC4
1 | package com.example.WarmUp; |
简单提及一下要用到的指令
1 | //控制台 |
frida的几种模式(彩蛋)
1 | 先frida启动 |
法一:直接抄,然后解就行
1 | import base64 |
感谢cdm格格送来的脚本
法二:动态调试
因为rc4的加密特殊性我们采用输入 111111111111111111111111111111111来直接查看最后结果的方式反推
不过多赘述了,相同方法参见sctf sbox那题
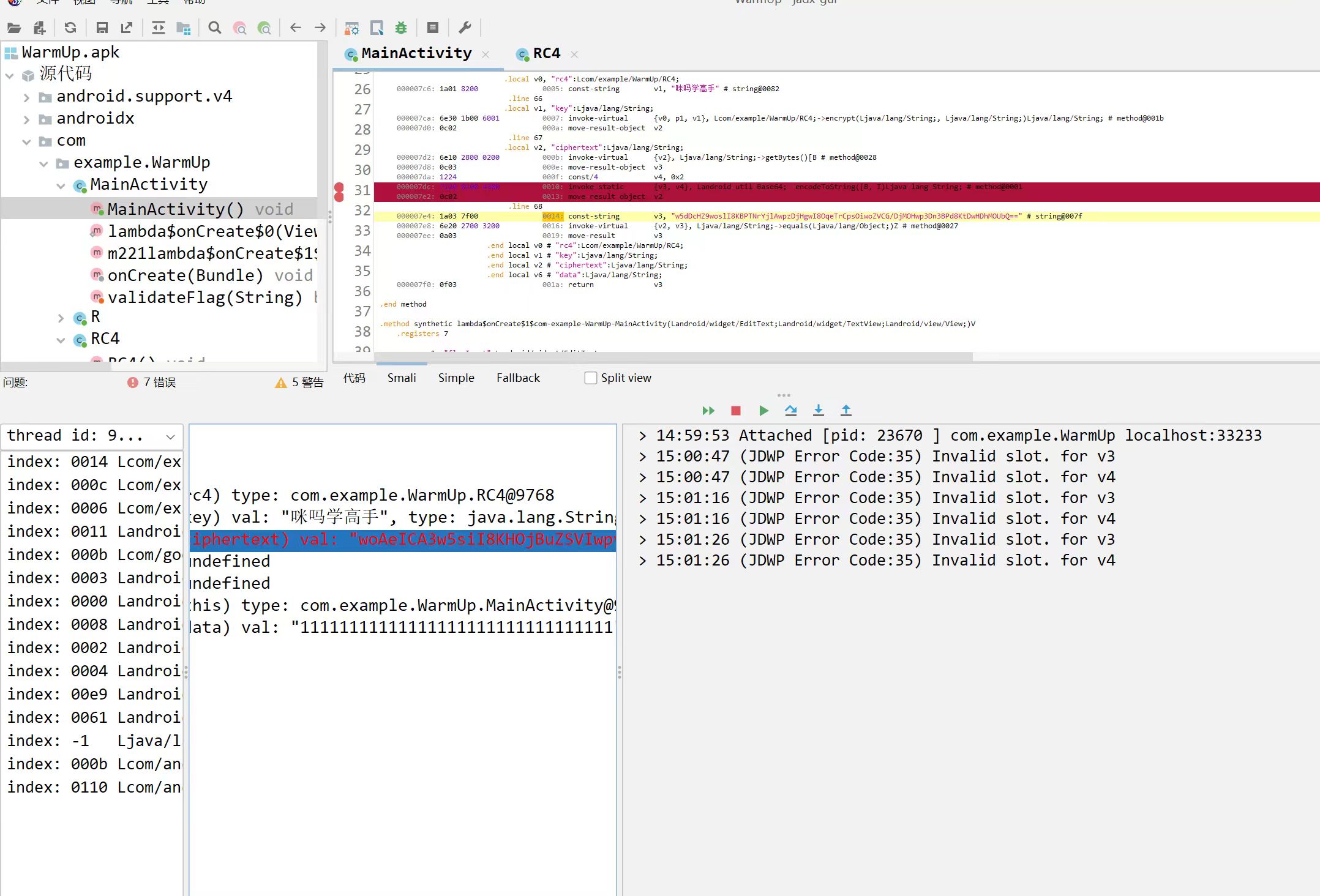
贴个脚本
1 |
|
没错,确实有问题,所以我们将使用第二种方法去取更精准的值
法三: frida_hook取值
我们要hook rc4加密后的返回结果
这是很经典的一个hook模板了
1 | function hook2() { |
结果
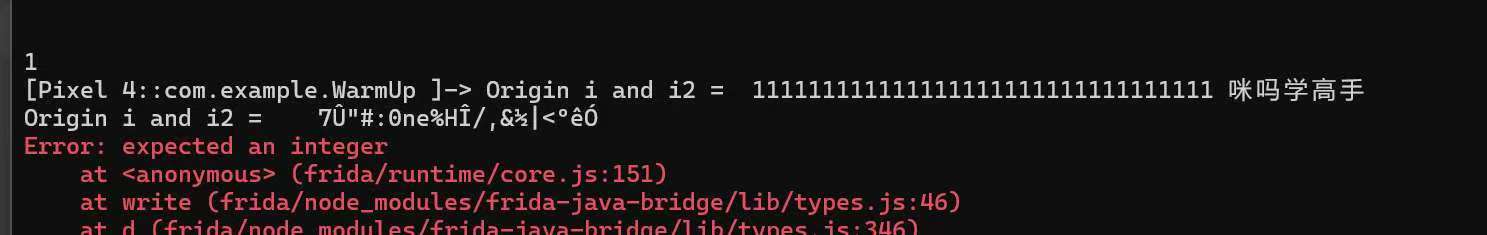
那么,我们用java转16进制即可
1 | function stringToByte(str) { |
结果
1 | [Pixel 4::com.example.WarmUp ]-> Origin i and i2 = 1111111111111111111111111111111 咪吗学高手 |
没错,成功了,但是转念一想,既然输出多少有点问题,为什么不直接取值然后顺便就异或回去呢,只要脚本写在一起就行
先看一下怎么用他的导入包函数
脚本
1 | setImmediate(function () { |
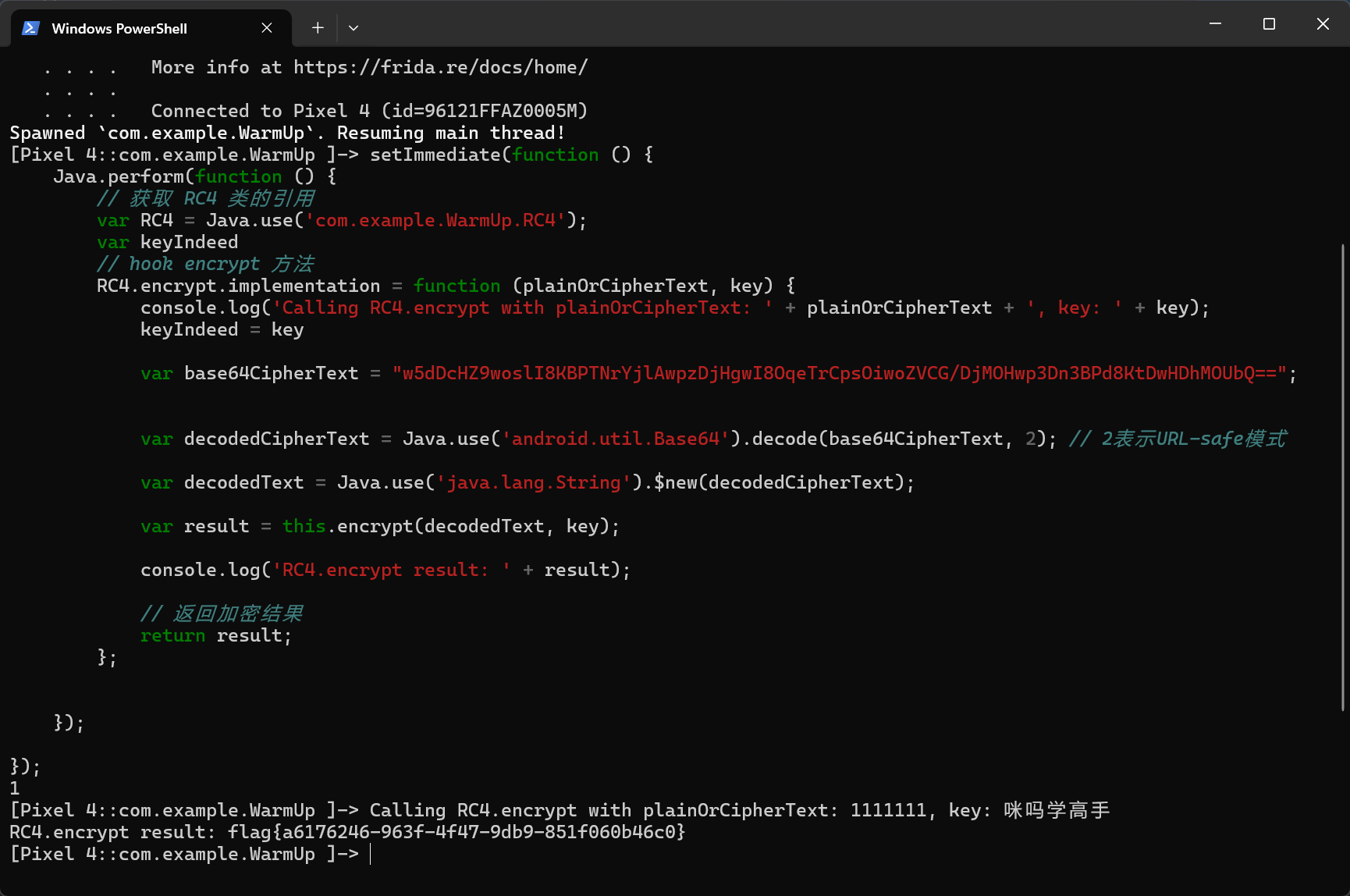
也确实成功了
法四:暴力内存搜刮
1 | https://www.52pojie.cn/thread-1838539-1-1.html |
有点复杂,具体去看正己师傅的文章
主要是要换frida环境
1 | pip install virtualenvwrapper-win -i https://pypi.tuna.tsinghua.edu.cn/simple |
命令
1 | objection -g com.example.saga131 explore |
1 | android hooking list activities -查看内存中加载的activity /android hooking list services -查看内存中加载的services |
1 | android intent launch_activity 类名 -启动activity或service(可以用于一些没有验证的activity,在一些简单的ctf中有时候可以出奇效) |
首先我们需要一个hashcode
1 | com.example.WarmUp on (google: 10) [usb] # android heap search instances com.example.WarmUp.MainActivity |

1 | android heap execute <handle> getPublicInt(实例的hashcode+方法名) //这里要求无参数,待会再找个无参数demo实验 |
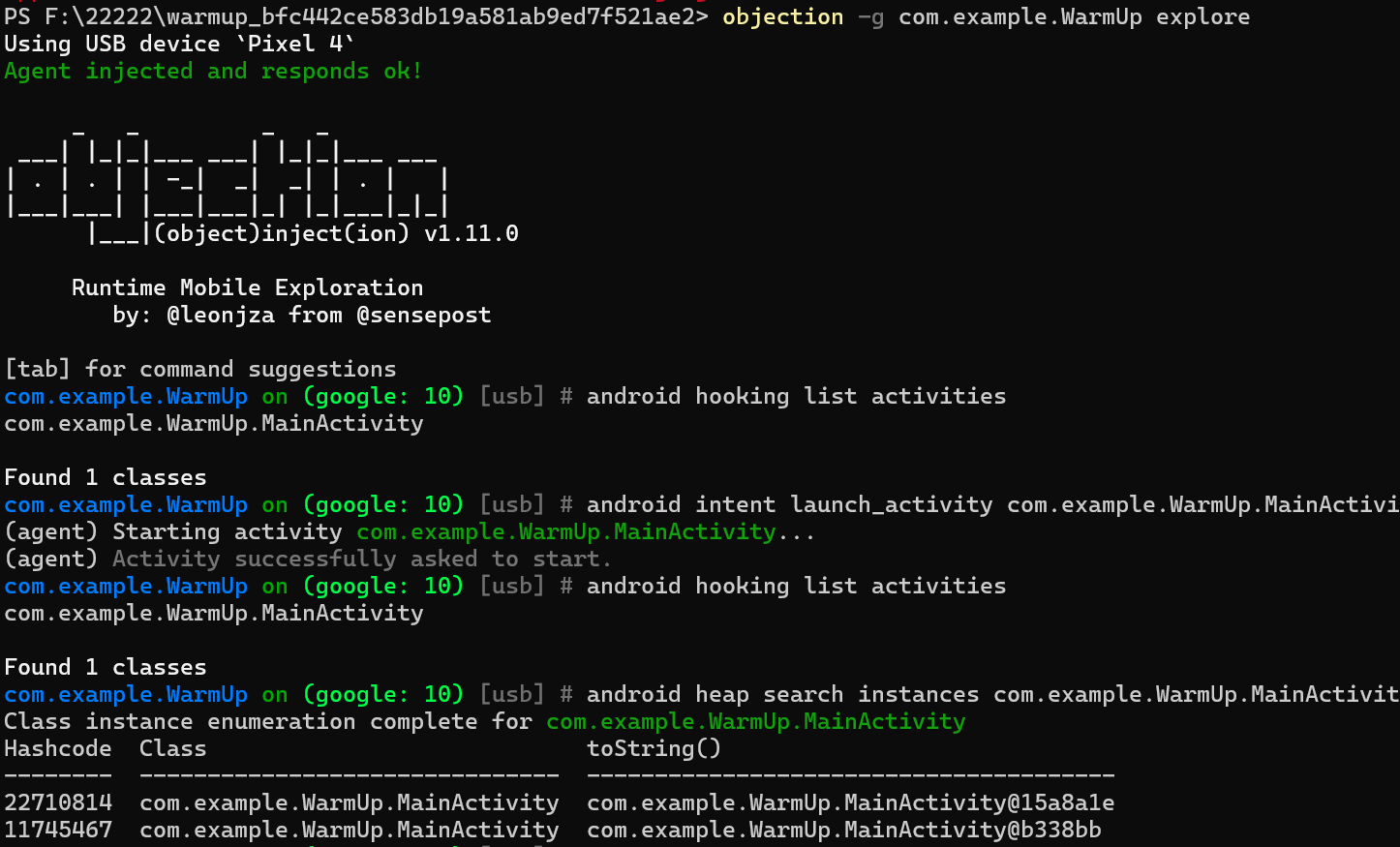
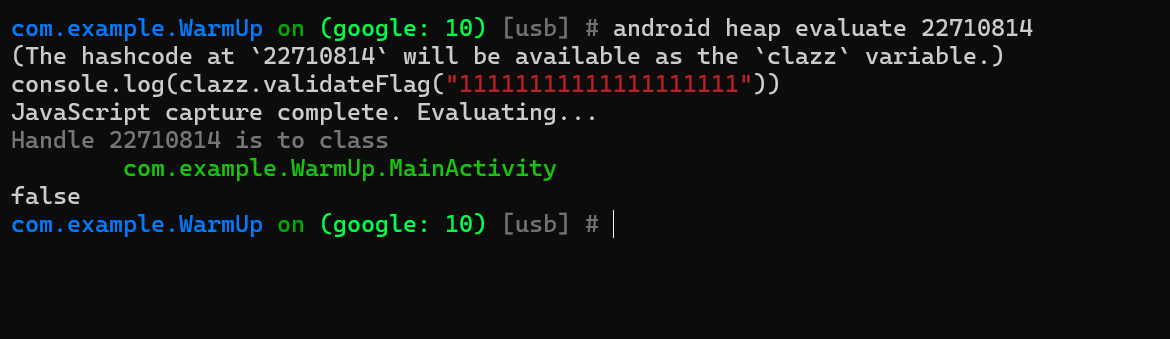
当然,还能用方法
1 | android hooking list class_methods com.example.WarmUp.MainActivity 类名 -内存漫游类中的所有方法 |
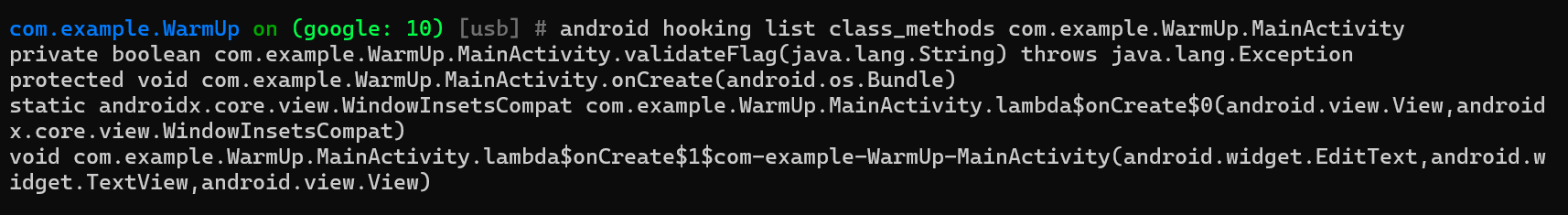
1 | android hooking watch class_method 类名.方法名 --dump-args --dump-return --dump-backtrace |
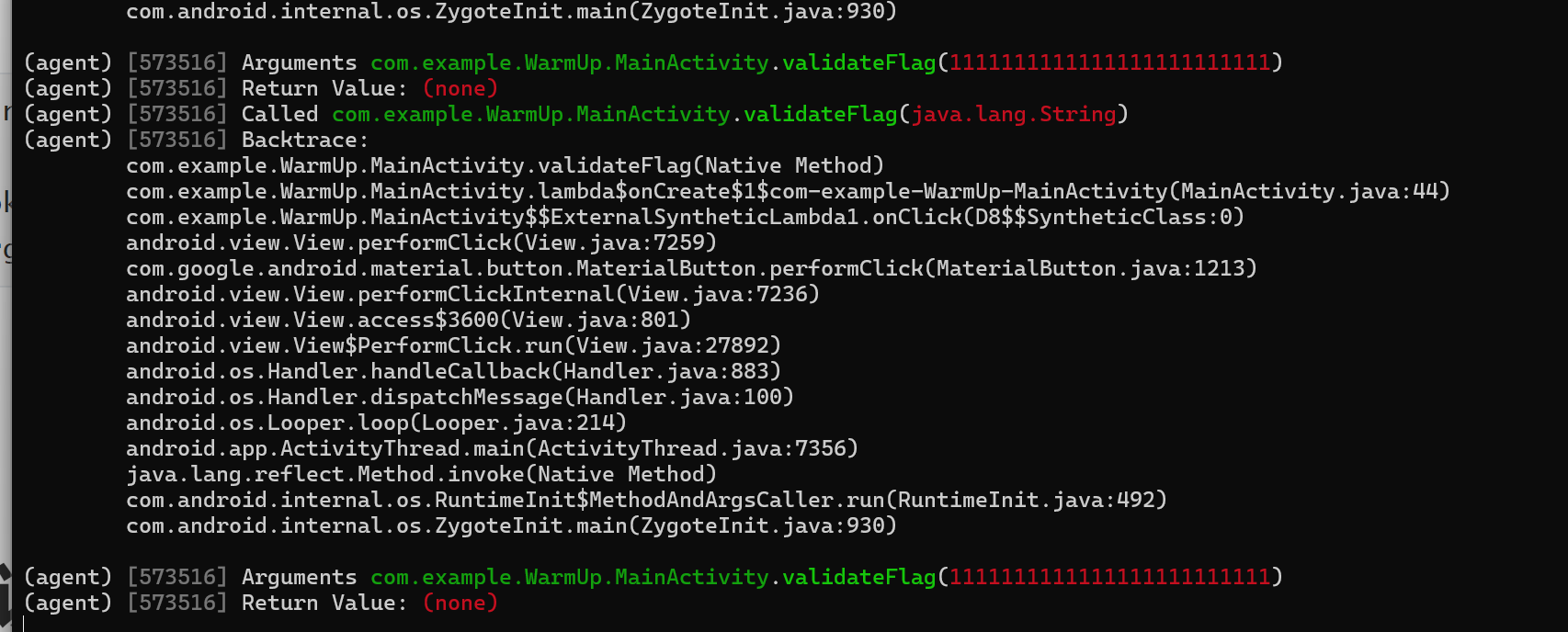
开始正题
所实话,感觉有点像java层模拟执行
有个问题,就是你会发现他搜不到这个RC4类,可以给大家看一下我之前的内存寻找结果
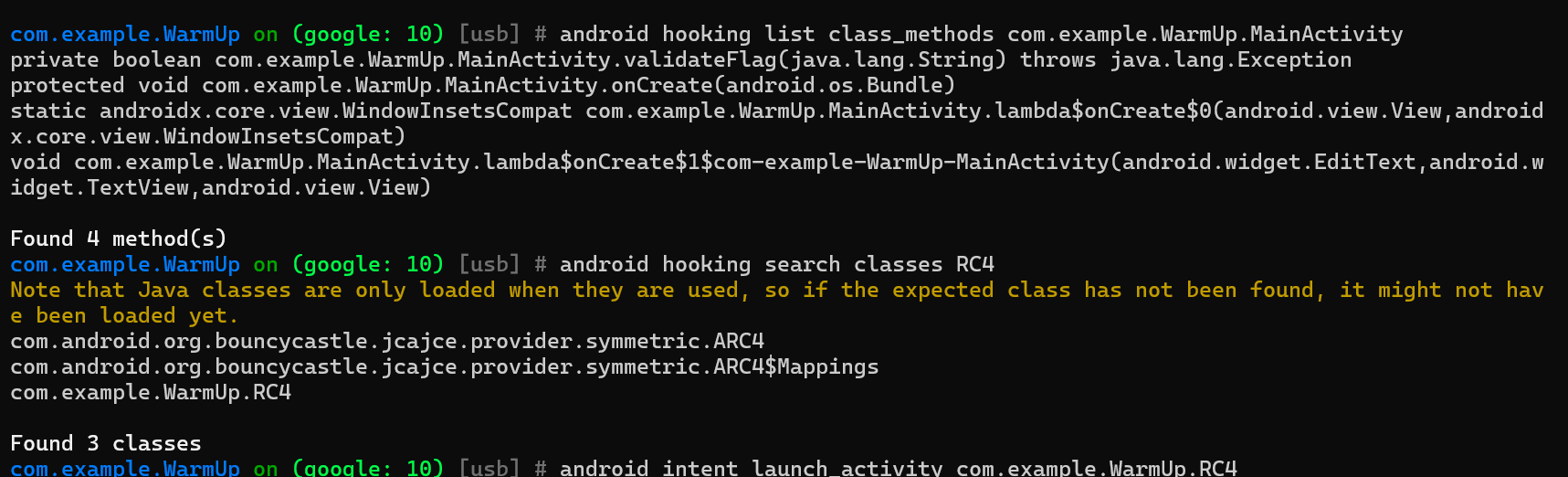
所以,我们得多点几下check,让他抓到,再人为搜索
1 | com.example.WarmUp on (google: 10) [usb] # android hooking search classes RC4 |
找个hashcode先
1 | com.example.WarmUp on (google: 10) [usb] # android heap search instances com.example.WarmUp.RC4 |
1 | com.example.WarmUp on (google: 10) [usb] # android heap evaluate 108025448 |
额,没区别啊,…….,感觉得想个办法,最好使用16进制的格式输出
不过找到了objection其他好玩的功能
1 | https://www.anquanke.com/post/id/197657 |
有个辅助写frida的
1 | android hooking generate simple com.example.WarmUp.RC4 |
效果
1 | Java.perform(function() { |
必要的知识掌握
有个超级好看的文章,建议都去学一下
1 | https://www.52pojie.cn/thread-742686-1-1.html |
先加个debuggable再找一下入口函数
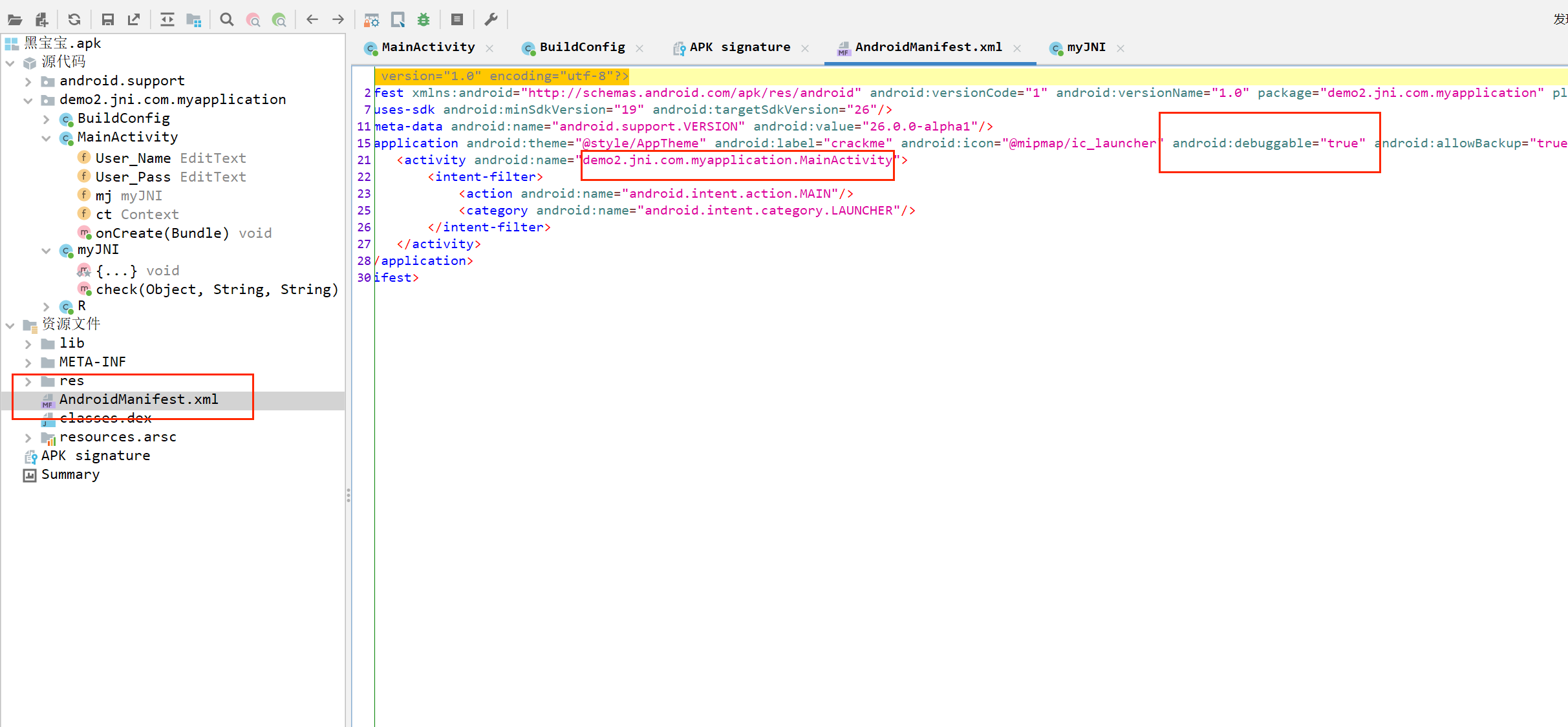
小插件
可以帮助分析so层的
1 | https://github.com/Pr0214/trace_natives |
大家真可以去下下这个,好有意思的小.py文件
frida检测绕过
GitHub - Ylarod/Florida: 基础反检测 frida-server / Basic anti-detection frida-server
download
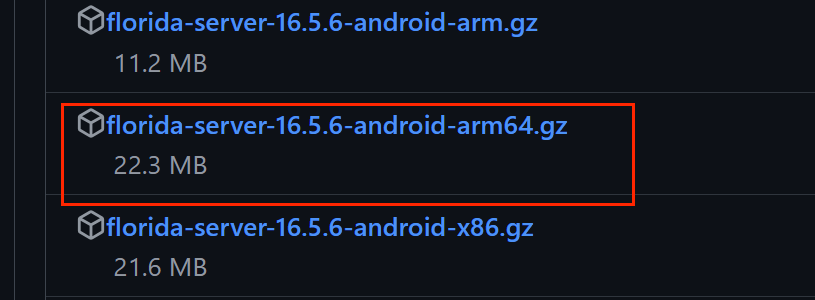
下载16.5.6这个
然后用法和frida一样
1 | frida -U -f com.jjkk.showmaker |
