国成杯&polar碎碎念
国成杯赛后复盘
额,总结就是在做 apk 的时候,那半自动化脚本给我搓破防了,而且有点神志不清了,看下文吧…..
Crush’s_secret
遇到这种smc我一般都是动调过去,然后按个p重新反编译就行,不多讲了,贴个原生态xxtea脚本吧
1 |
|
round
欸,又是被dfs算法卡住的一集
先讲怎么过username
1 | android:debuggable="true" |
mt管理器改上,保存,签名不过的话自己签一个就行,然后输入1111111111调试,发现加密后和cyber对比中间两位对调,问题不大
然后讲后面的passport
1 | 有个makebox,可以调起来来,或者直接嗦ai,记得看一下对比 |
然后开始最头疼的一集,给大家看看我的goushi半自动化脚本
1 |
|
欸,所以还得是dfs
python版,从哈工大师傅的wp偷的
1 | def makebox(s): |
C语言版,showmaker师傅友情泄露
欸?他base64脚本也挺好的,全偷了o_0
1 |
|
dfs.c
1 |
|
欸,太强了(挠屁股.jpg)
eazykey
不会内核,跟着别的师傅的wp复现(
1 | https://lilachit.notion.site/2024-Re-Pwn-WP-by-Lilac-2698b2aad54d420dac920fbdee1fb5d4 |
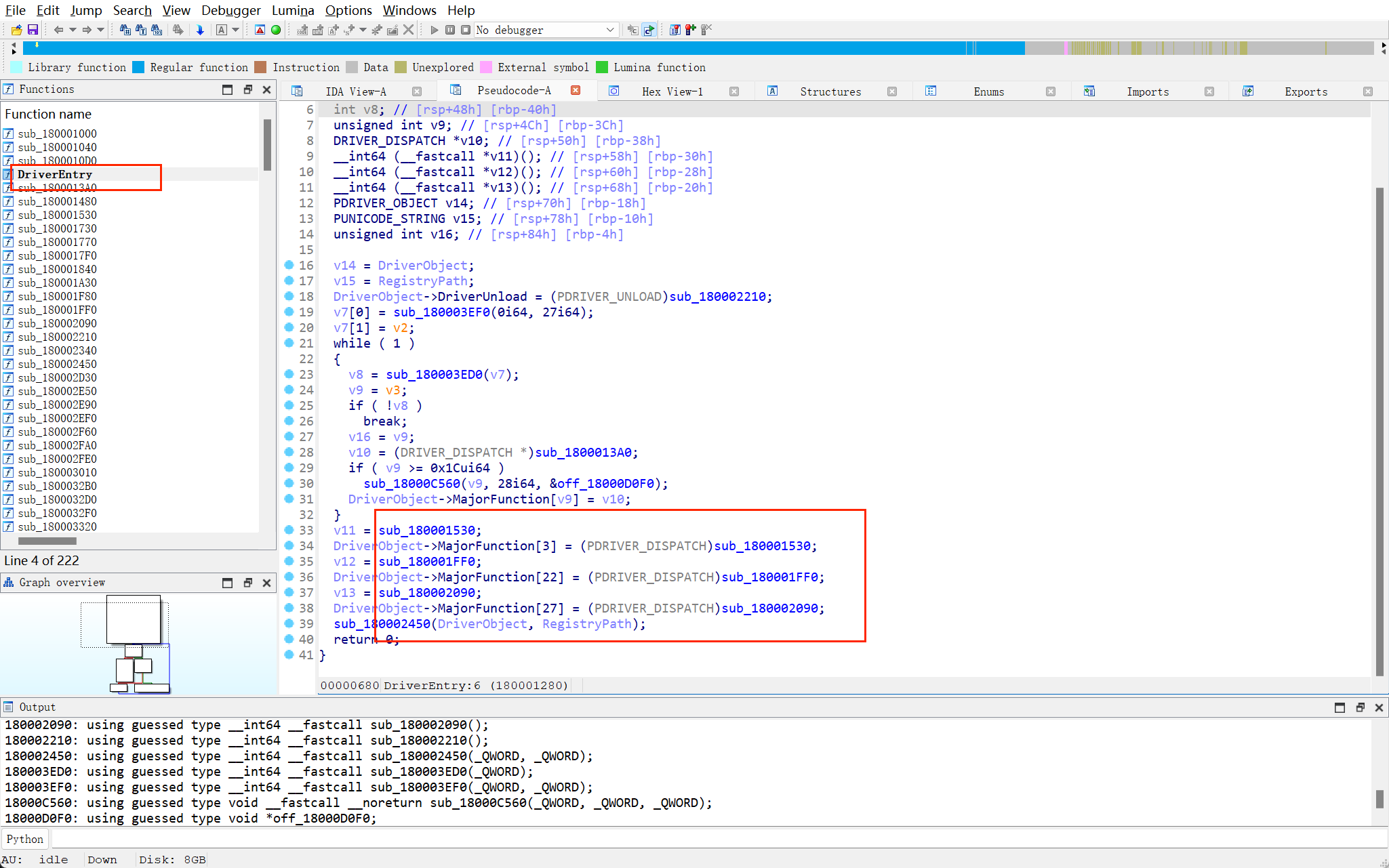
找入口,然后找主逻辑
v11
1 | 这个函数 sub_180001530 是一个 Windows 驱动程序中的 I/O 请求处理函数,负责处理与 IRP 相关的 I/O 请求。 |
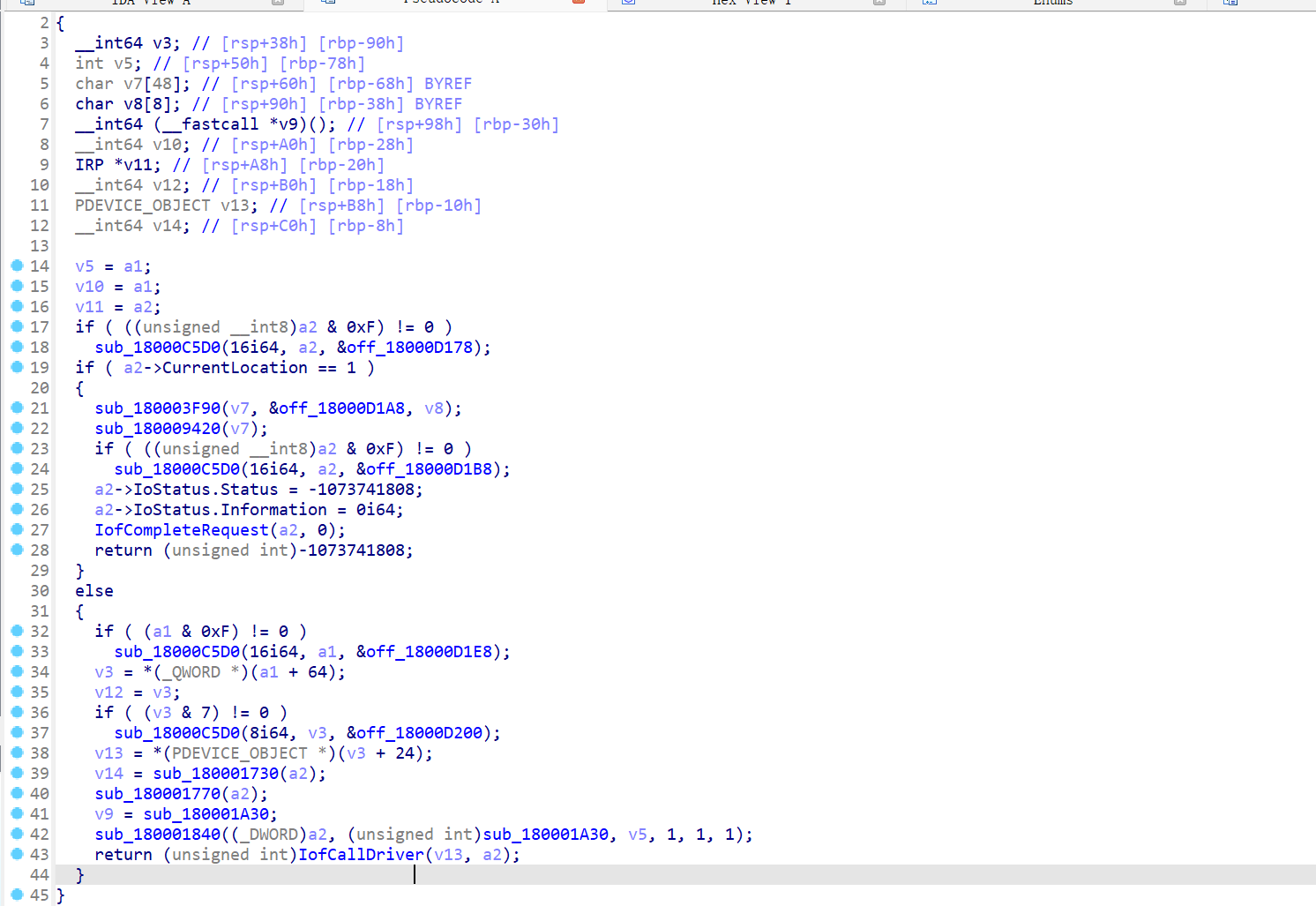
v12
1 | sub_180001FF0 是一个处理电源管理和 I/O 请求的函数。它的主要步骤包括: |
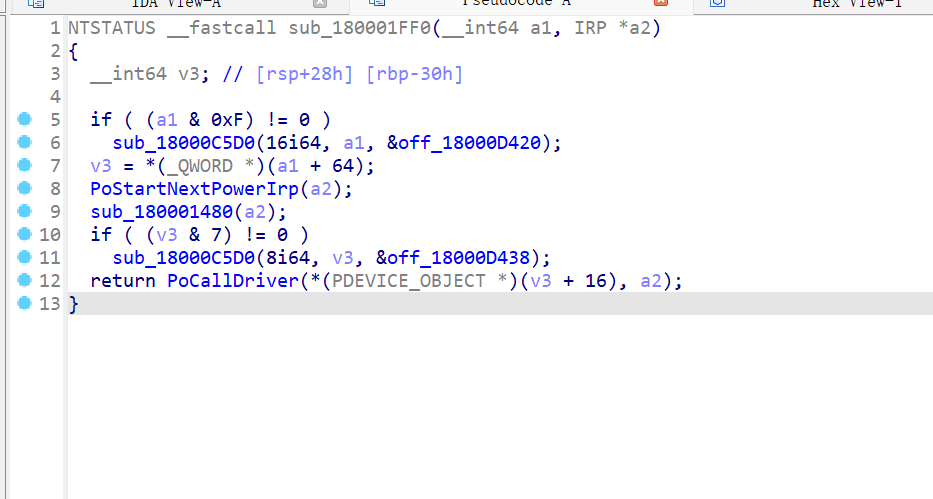
v13
1 | sub_18000C5D0:这是一个处理内存对齐的函数。如果某个对象的地址不是合适的对齐,它会处理并调整。 |
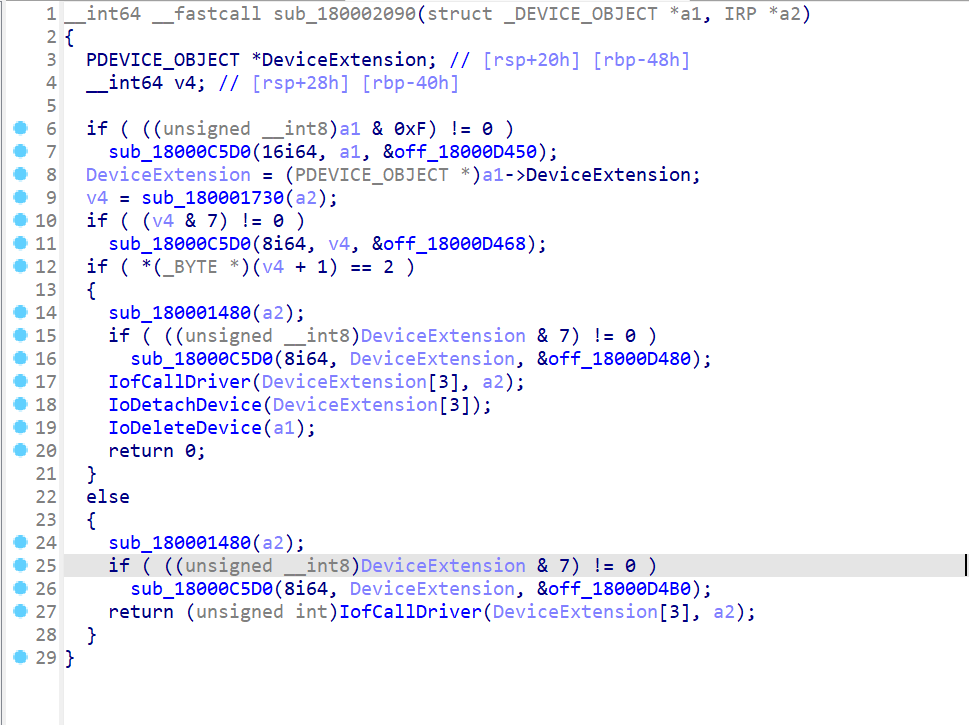
显然,v11因该是个read,比较可疑,其实感觉这里已经可以根据wp猜测这是个键盘驱动了
一个个点开来看
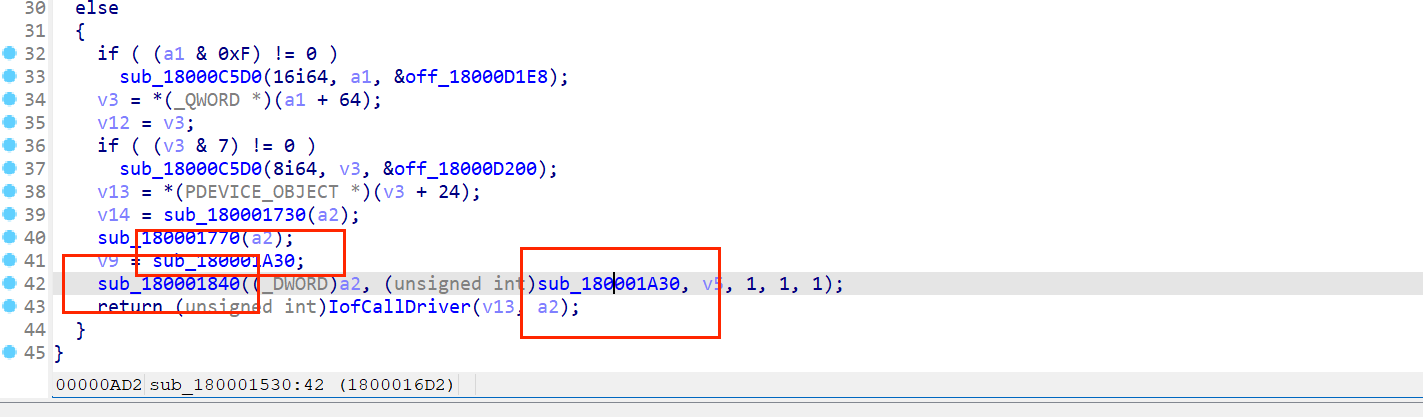
这里有些奇怪的东西
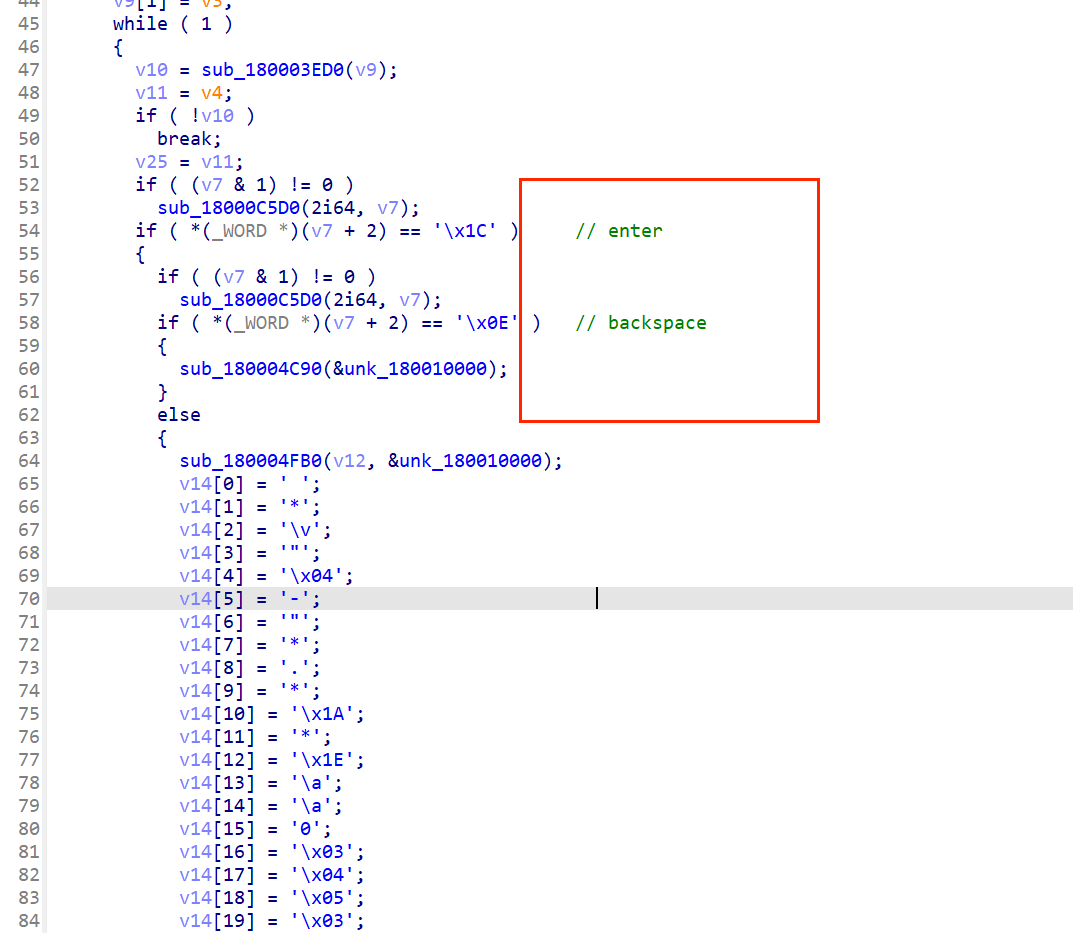
那么enter过后一般是不是就要检查了
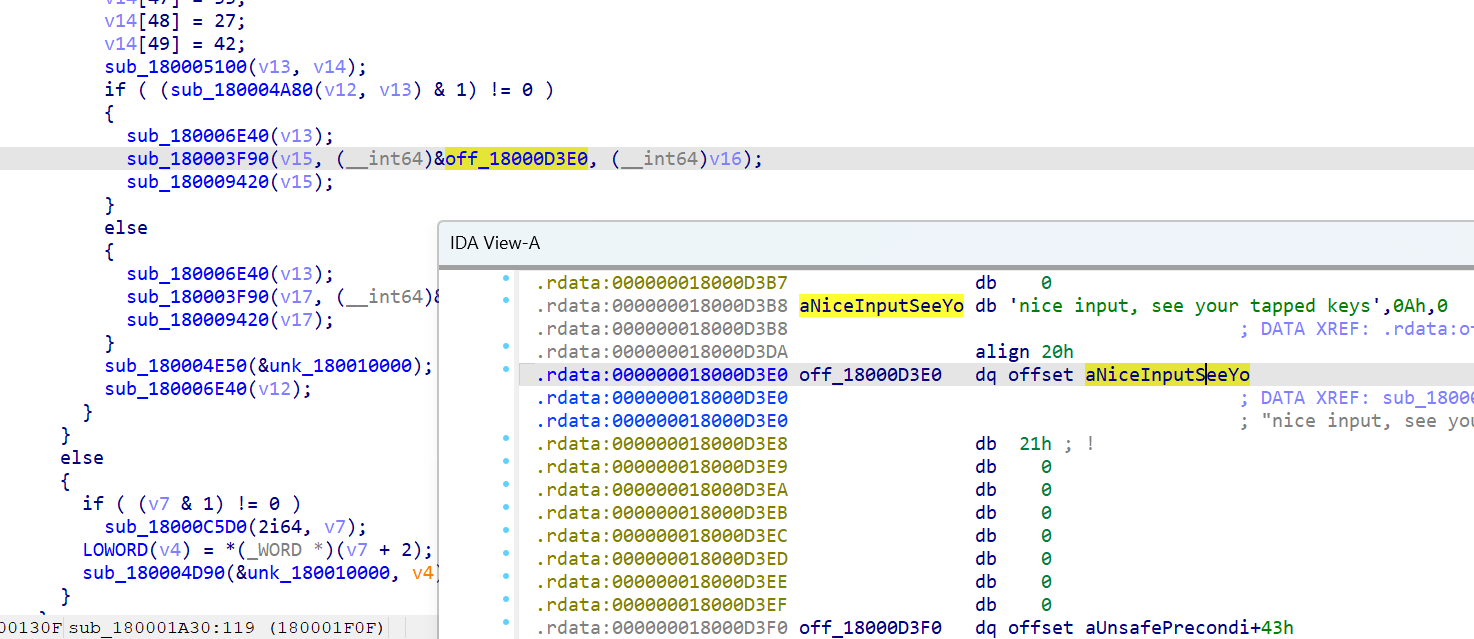
确实,根据字符串提示应该是了
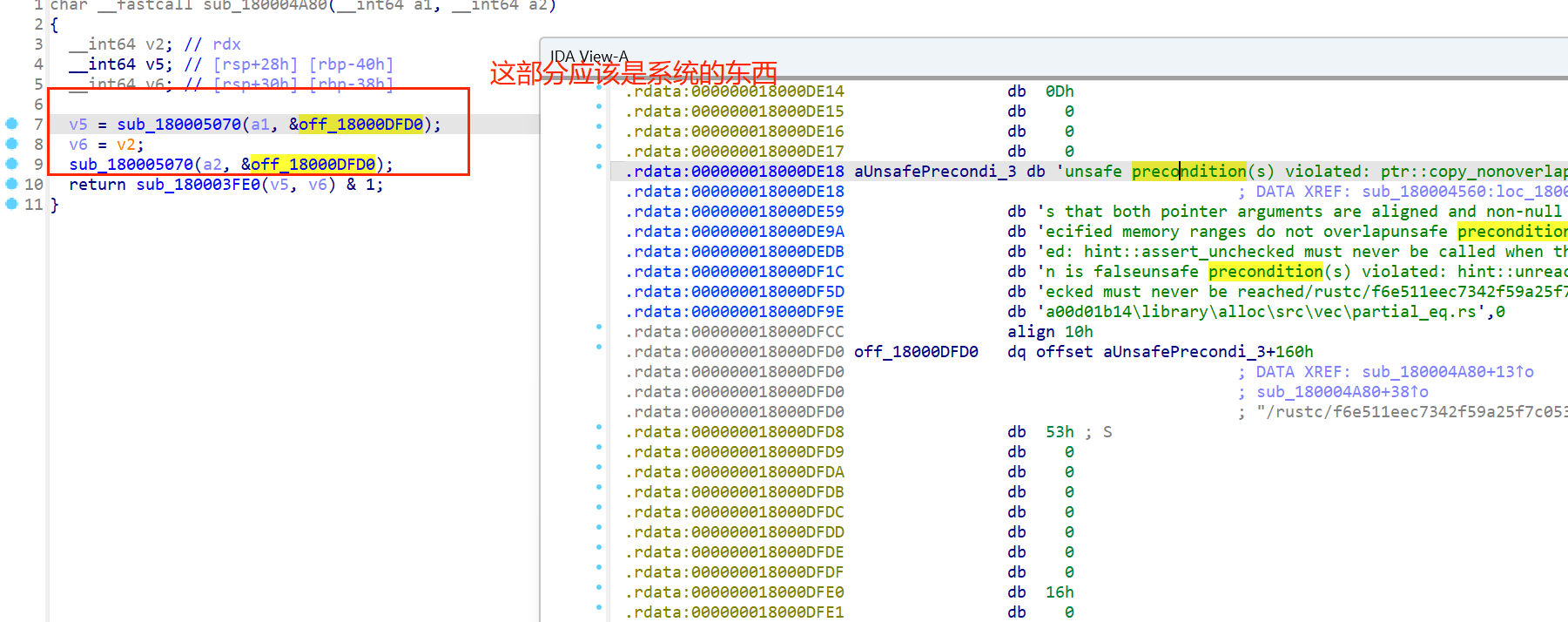
很明显就是一个普通的对比,所以再根据墨水✌的wp,应该就是在键盘上敲对应的按键就行了
可以去这里找按键
1 | https://bbs.kanxue.com/thread-270393.htm |
或者问下ai
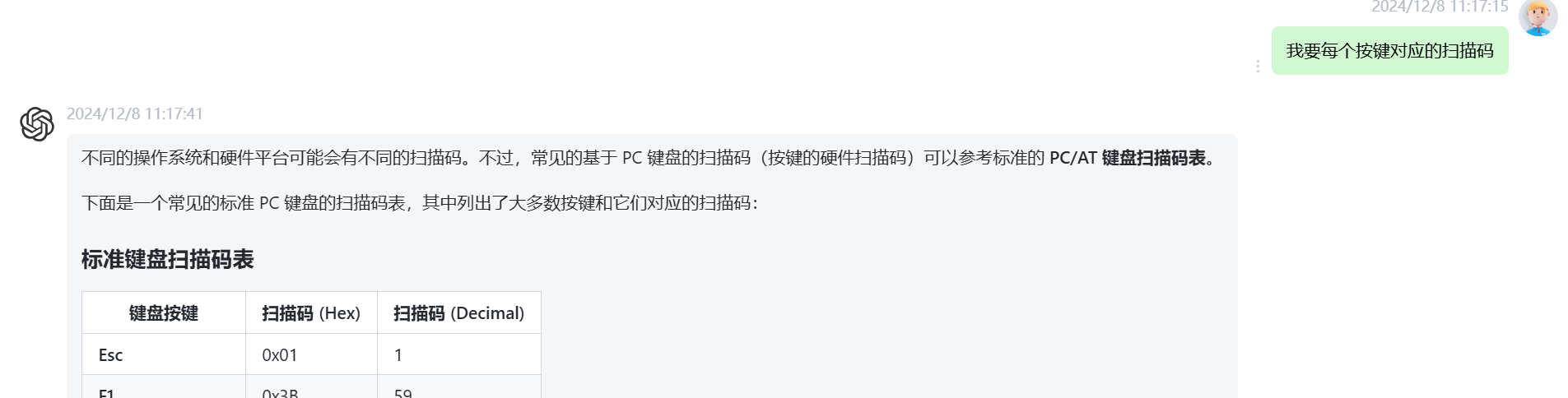
1 | 键盘按键 扫描码 (Hex) 扫描码 (Decimal) |
再对应写个脚本就行
1 | keys = [32,42,11,34,4,45,34,42,46,42, 26, 42, 30, 7, 7, 48, 3, 4, 5, 3, 12, 11, 5, 32, 5, 12, 5, 7, 9, 30, 12, 10, 10, 32 , 4, 12, 8, 18, 32, 48, 30, 5, 46, 10, 11, 11, 2, 33, 27, 42] |
polar赛后复盘
本来上次打了就不想再打了,但是还是过来看看有什么有意思的题,每次都让人出乎意料
o_0
我以为die没查出来,原来是我眼瞎了
Mac 的运行程序 arm 64位
好难看啊
没运行环境,裂开,静态分析一下
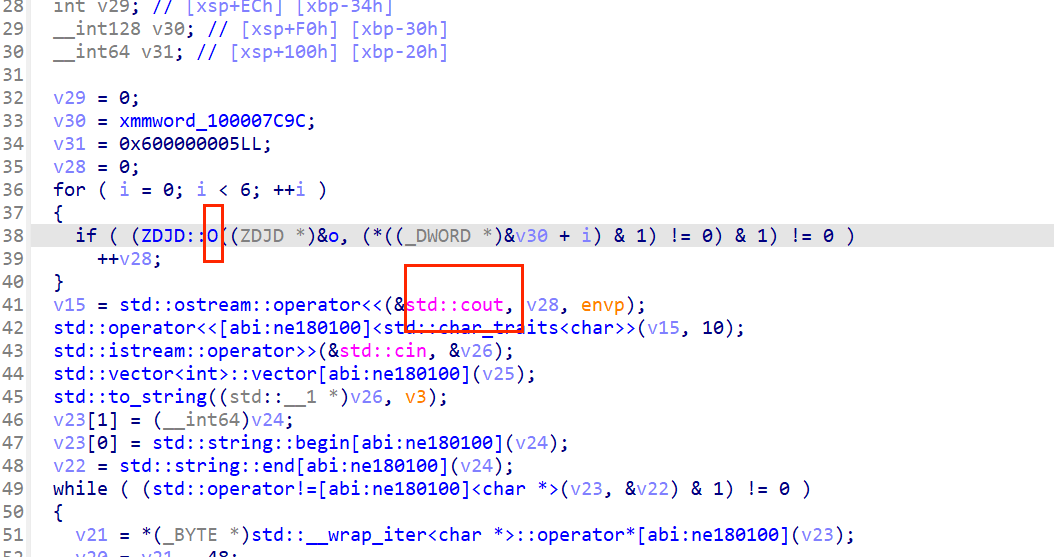
注意,这里0就是一个函数了,就是判断奇数偶数
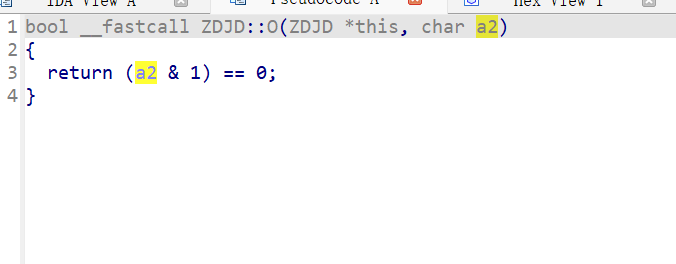
v30
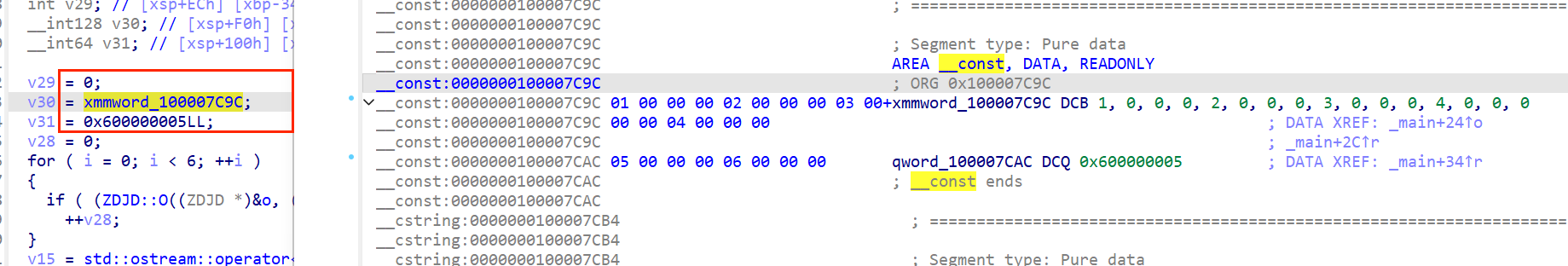
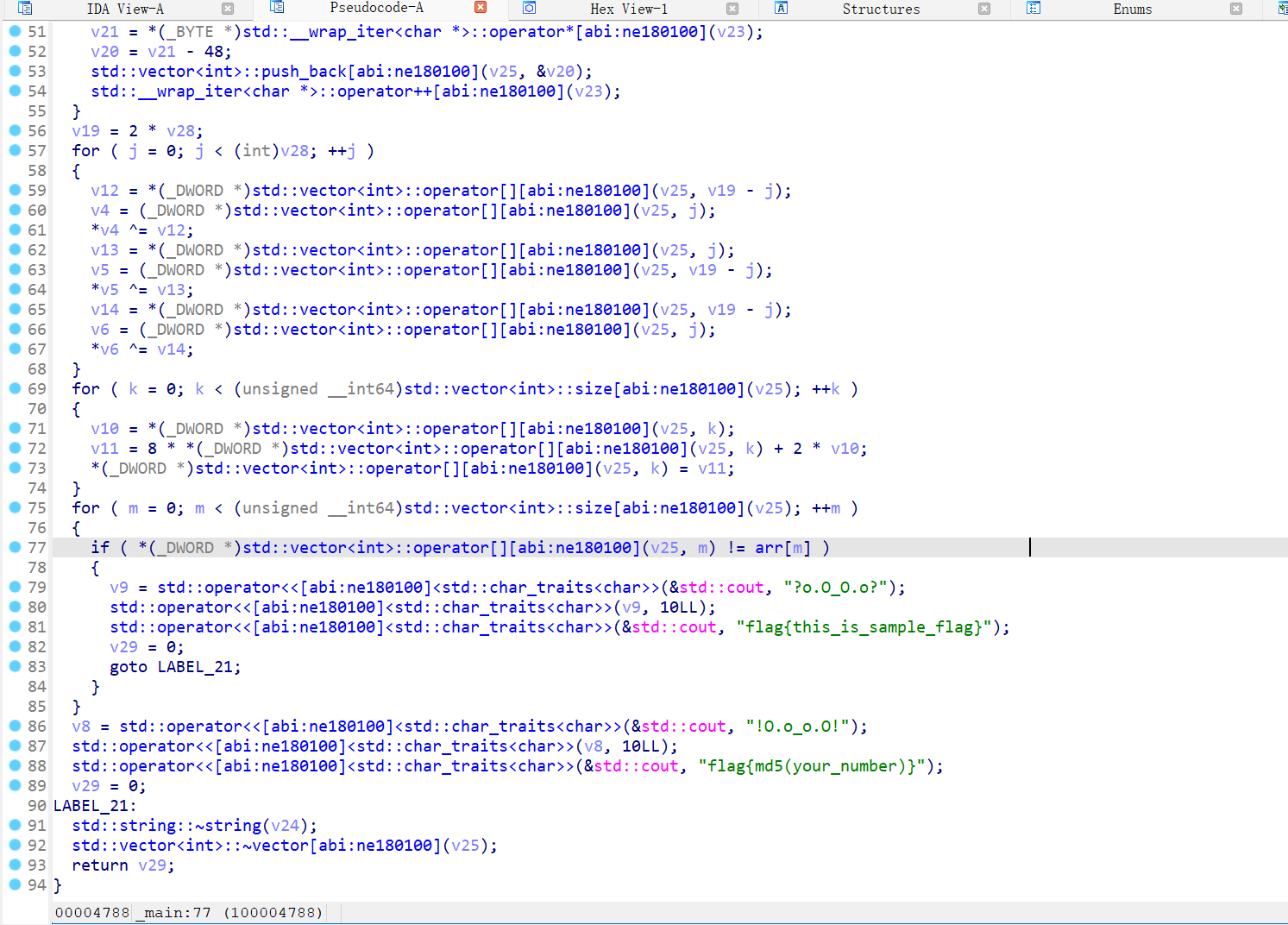
然后就是分析加密流程
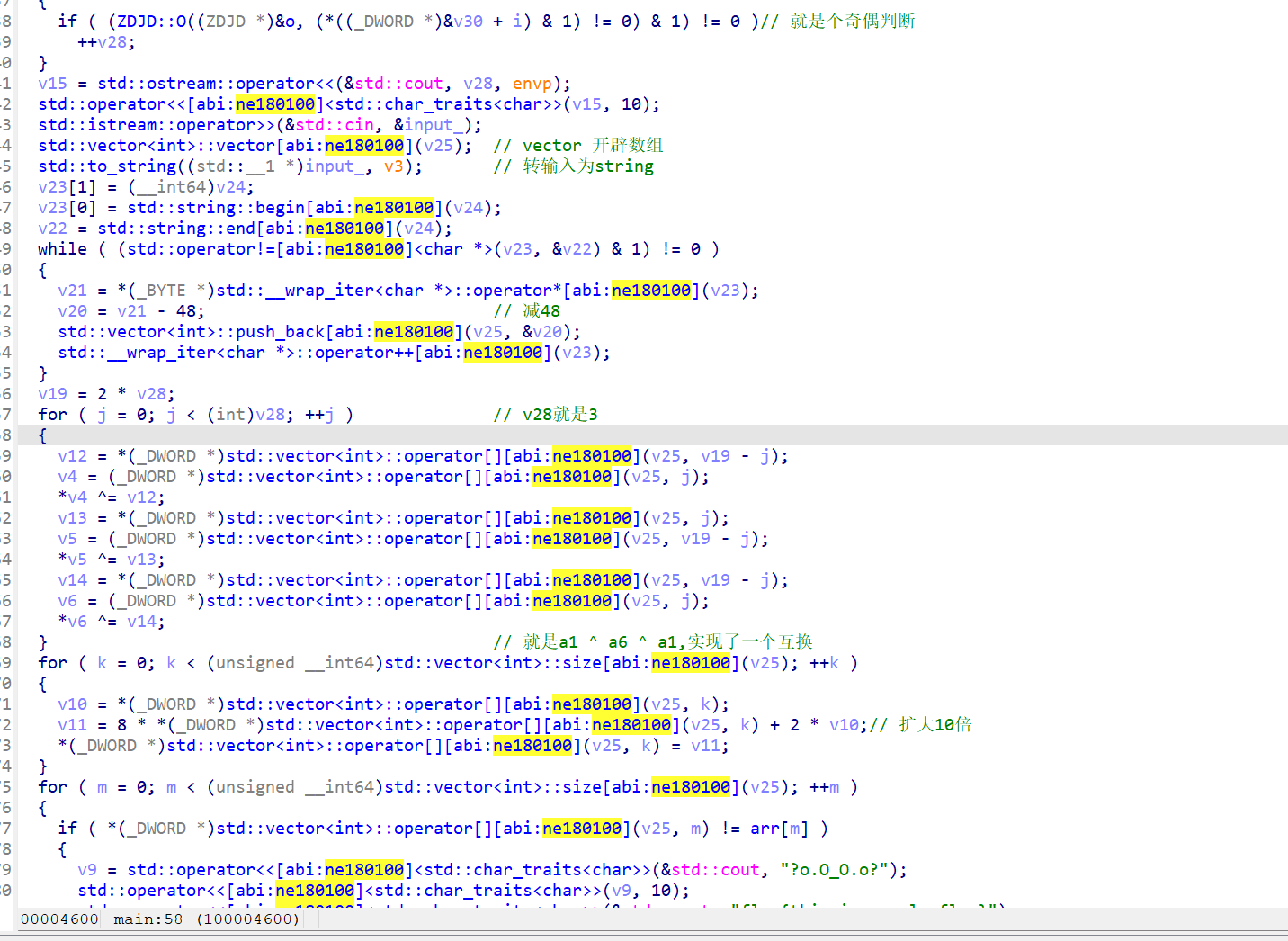
最后的比较
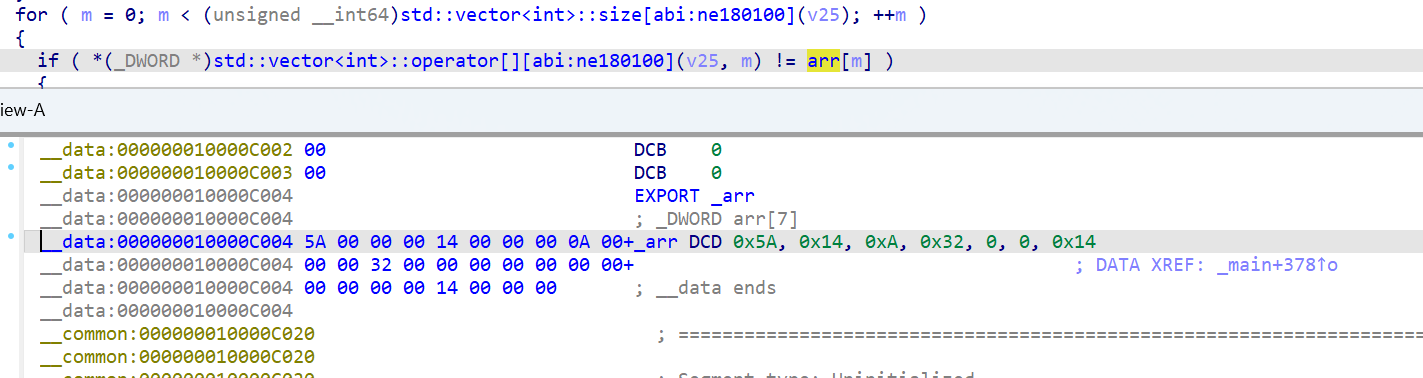
这里学到点新的数组索引方式
1 | v4 = (_DWORD *)std::vector<int>::operator[][abi:ne180100](v25, j); |
decipher
经典3.9以上,这玩意失效了,这次一定要配个好的
1 | uncompyle6 dialogue.pyc |
pycdc,别忘了放哪里了o.o
1 | F:\re_in_all\pyextra\afe4b-main\pycdc |
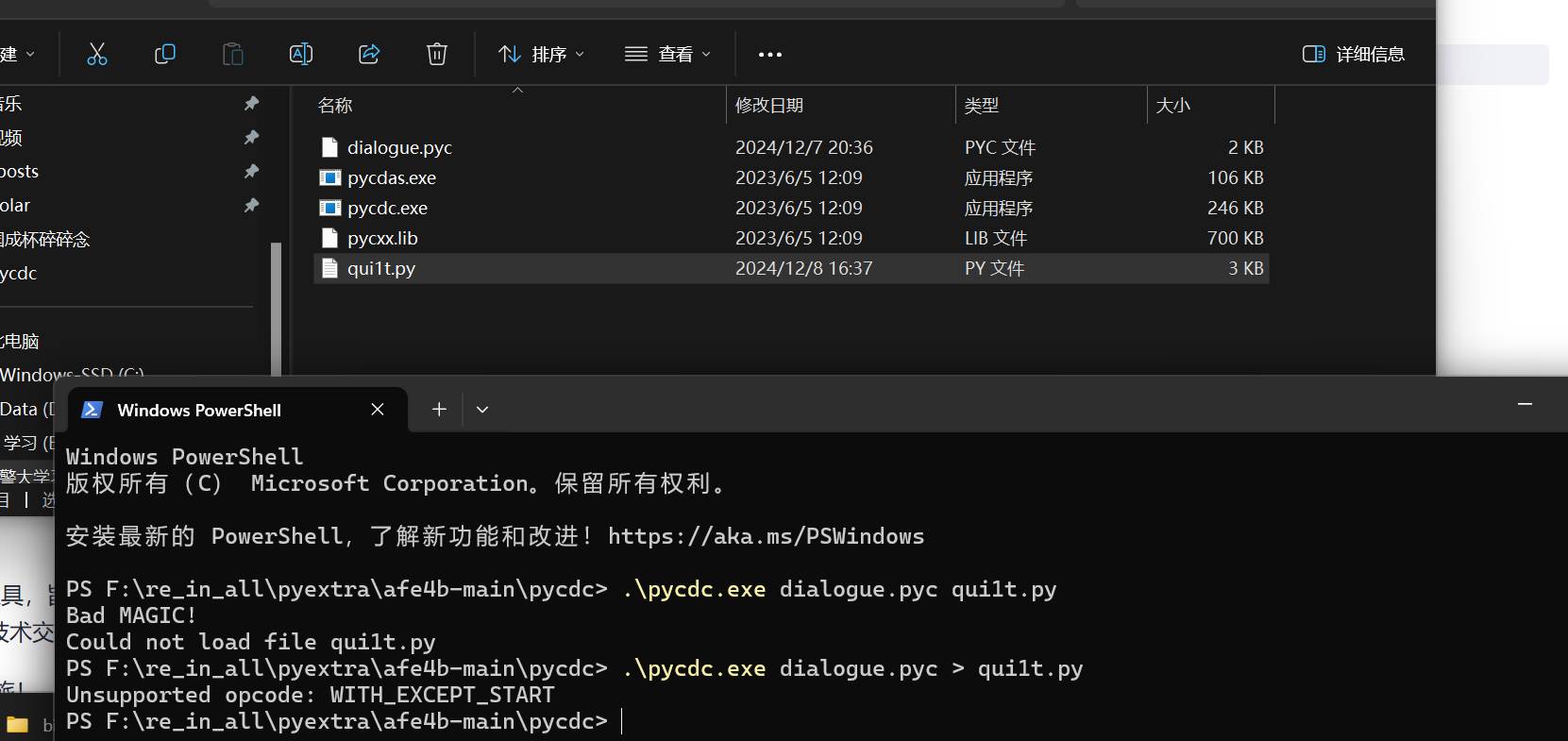
看看效果
1 | # Source Generated with Decompyle++ |
然后要手动改一部分
1 | key = PBKDF2(password, salt, 32, 1000000, **('dkLen', 'count')) |
ai🔒个解密脚本
1 | import os |
额…….
All articles on this blog are licensed under CC BY-NC-SA 4.0 unless otherwise stated.
Comments
ValineGitalk
