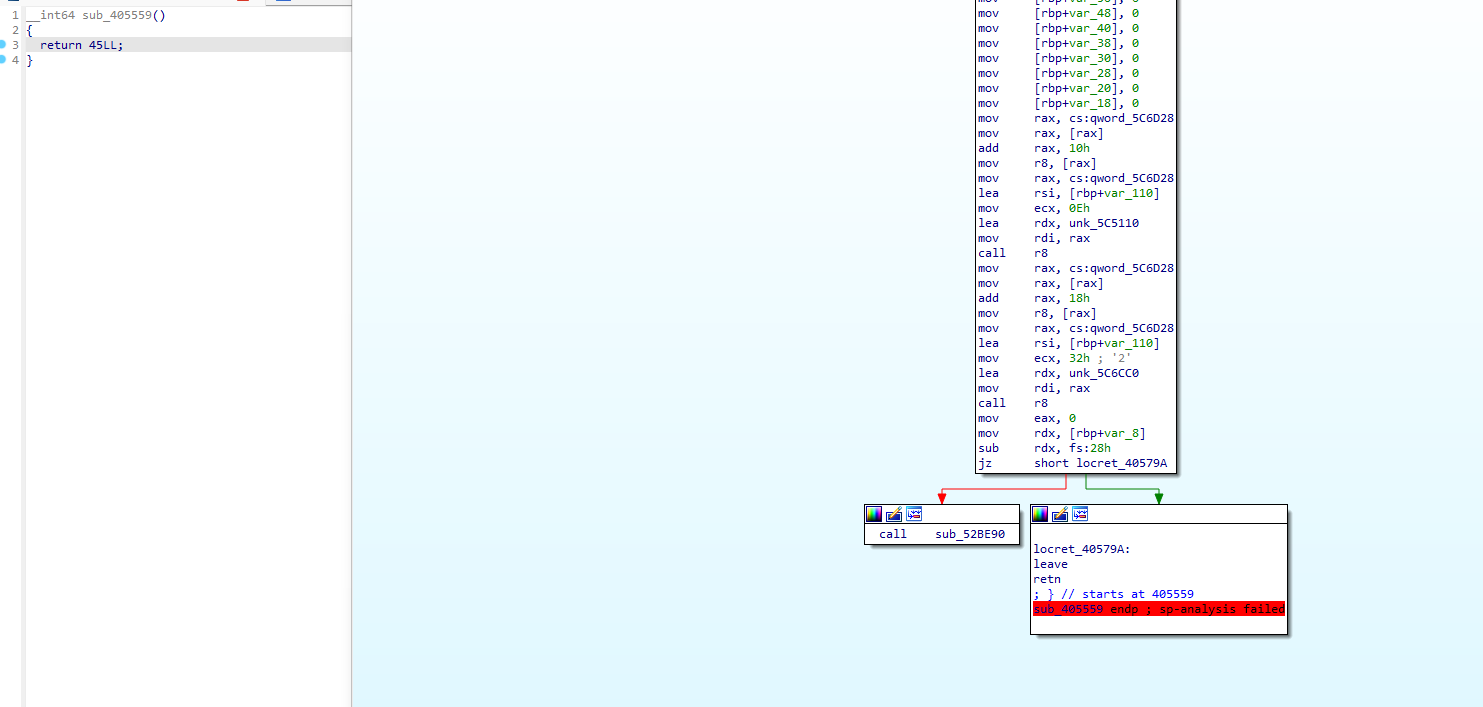
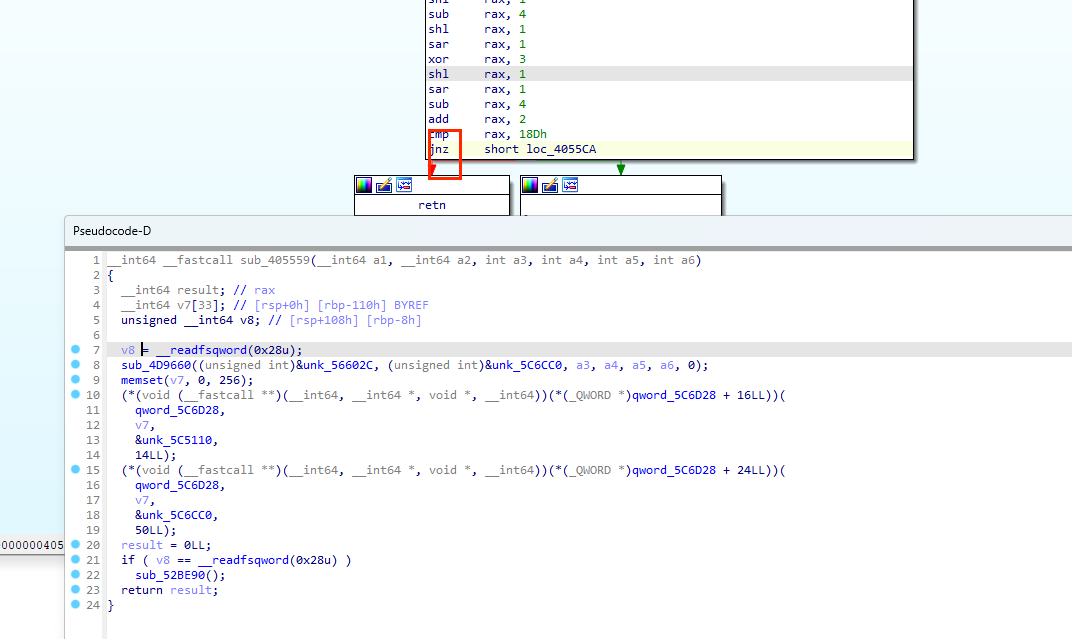
全国软件安全大赛赛后复盘 dontyousee 基本题,记录一个小技巧
改下跳转ida就识别出来了
但是调试过程中,得看着别改变文件本来的运行规律
happylock 复盘
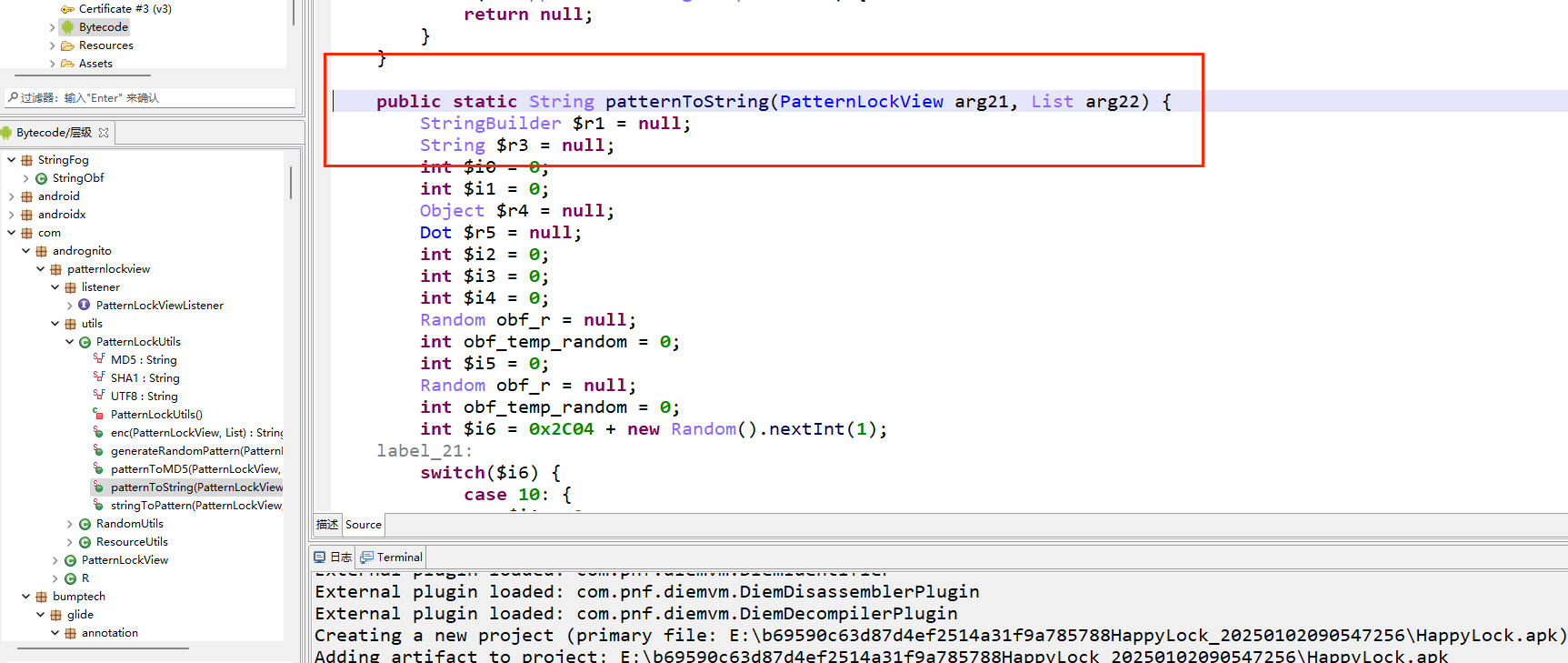
看一眼mainactivity,没啥,去看Utils
有个enc,
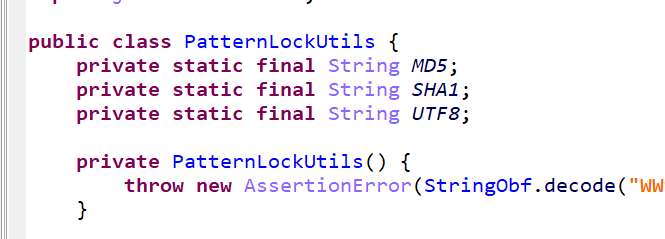
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 public class PatternLockUtils { private static final String MD5 ; private static final String SHA1 ; private static final String UTF8 ; private PatternLockUtils () { throw new AssertionError (StringObf .decode ("WW91IGNhbiBub3QgaW5zdGFudGlhdGUgdGhpcyBjbGFzcy4gVXNlIGl0cyBzdGF0aWMgdXRpbGl0eSBtZXRob2RzIGluc3RlYWQ=" )); } public static String enc (PatternLockView arg22, List arg23) throws NoSuchAlgorithmException , UnsupportedEncodingException { String $r2 = null ; MessageDigest $r3 = null ; String $r4 = null ; byte[] $r5 = null ; BigInteger $r6 = null ;
java我们知道,先有类再有对象,PatternLockUtils就是要调用主类,因为是static变量,所以只要加载PatternLockUtils,就一定会有enc加载,我们可以用frida,看看发生了什么
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 function hook1 ( var MainActivity = Java .use ('com.andrognito.patternlockview.utils.PatternLockUtils' ); var enc = MainActivity .enc ; enc.implementation = function (arg1, arg2 ) { console .log ("enc called " , arg1, arg2); var result = this .enc (arg1, arg2); console .log ("enc result " , result); return result; } } function main ( Java .perform (function ( hook1 (); }) } setImmediate (main);
1 2 3 4 5 6 7 8 9 10 >frida-ps -Ua PID Name Identifier ----- -------------- --------------------------------------- 20152 Chrome com.android.chrome 2824 Google com.google.android.googlequicksearchbox 18861 Google Play 商店 com.android.vending 20305 HappyLock com.crackme.happylock 19173 MT管理器 bin.mt.plus 19268 Magisk com.topjohnwu.magisk 19616 YouTube com.google.android.youtube
1 frida -U -f "com.crackme.happylock" -l hook.js
结果
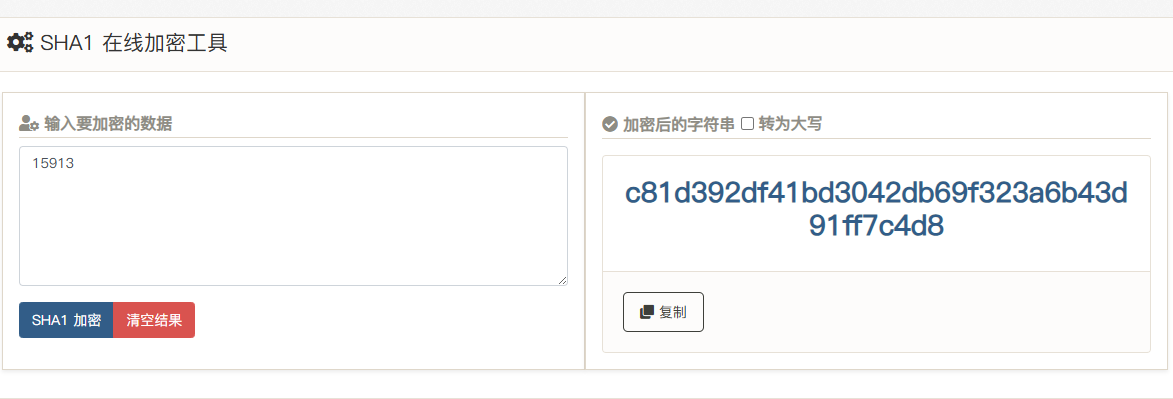
1 enc result c81d392df41bd3042db69f323a6b43d91ff7c4d8
同理,我们再分析一下这个
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 function hook1 ( var MainActivity = Java .use ('com.andrognito.patternlockview.utils.PatternLockUtils' ); var patternToString = MainActivity .patternToString ; patternToString.implementation = function (arg1, arg2 ) { console .log ("patternToString called " , arg1, arg2); var result = this .patternToString (arg1, arg2); console .log ("patternToString result " , result); return result; } var enc = MainActivity .enc ; enc.implementation = function (arg1, arg2 ) { console .log ("enc called " , arg1, arg2); var result = this .enc (arg1, arg2); console .log ("enc result " , result); return result; } } function main ( Java .perform (function ( hook1 (); }) } setImmediate (main);
我们发现,手势被数字代替了
1 2 patternToString result 15913 enc result c81d392df41bd3042db69f323a6b43d91ff7c4d8
再结合这个,我们可以猜测
但是,我们依然还没达到破解的目的
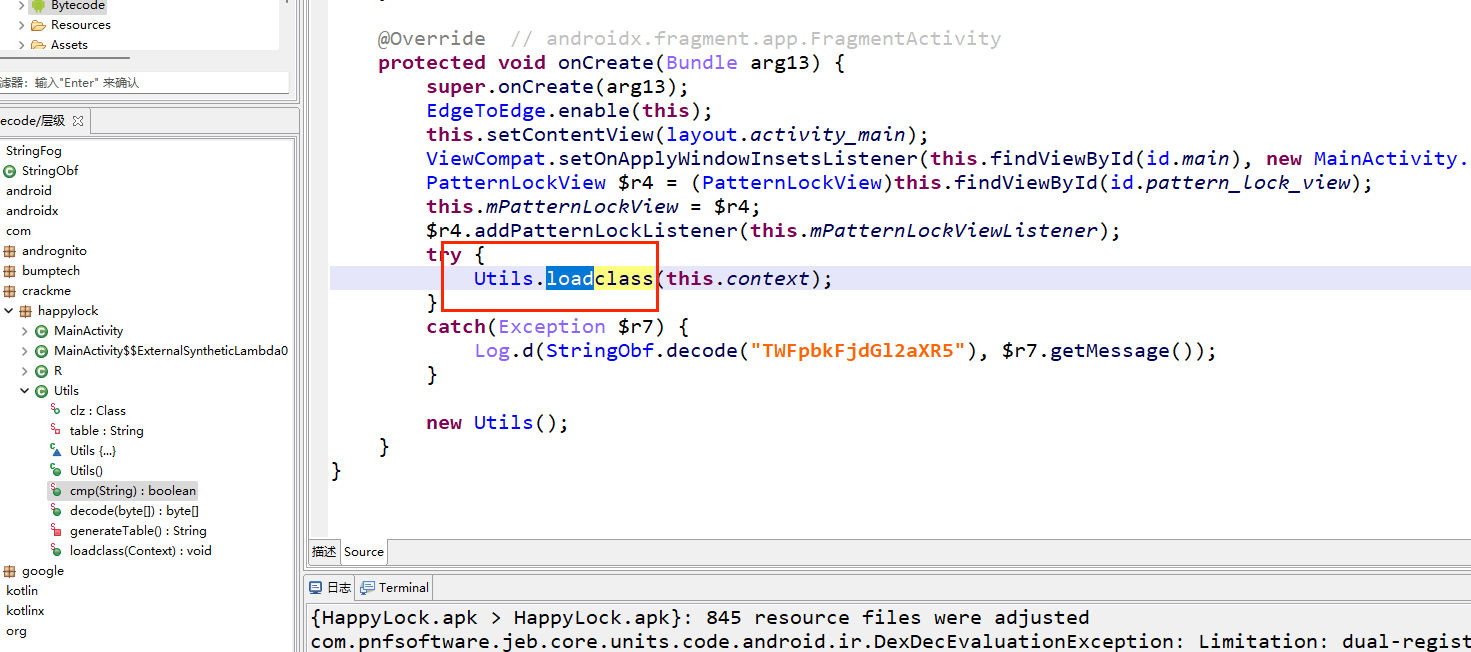
接着在cmp层发现一个load,前往so层
shift f7
先init array再jni load
1 2 adb forward tcp:23946 tcp:23946 adb shell input text ""
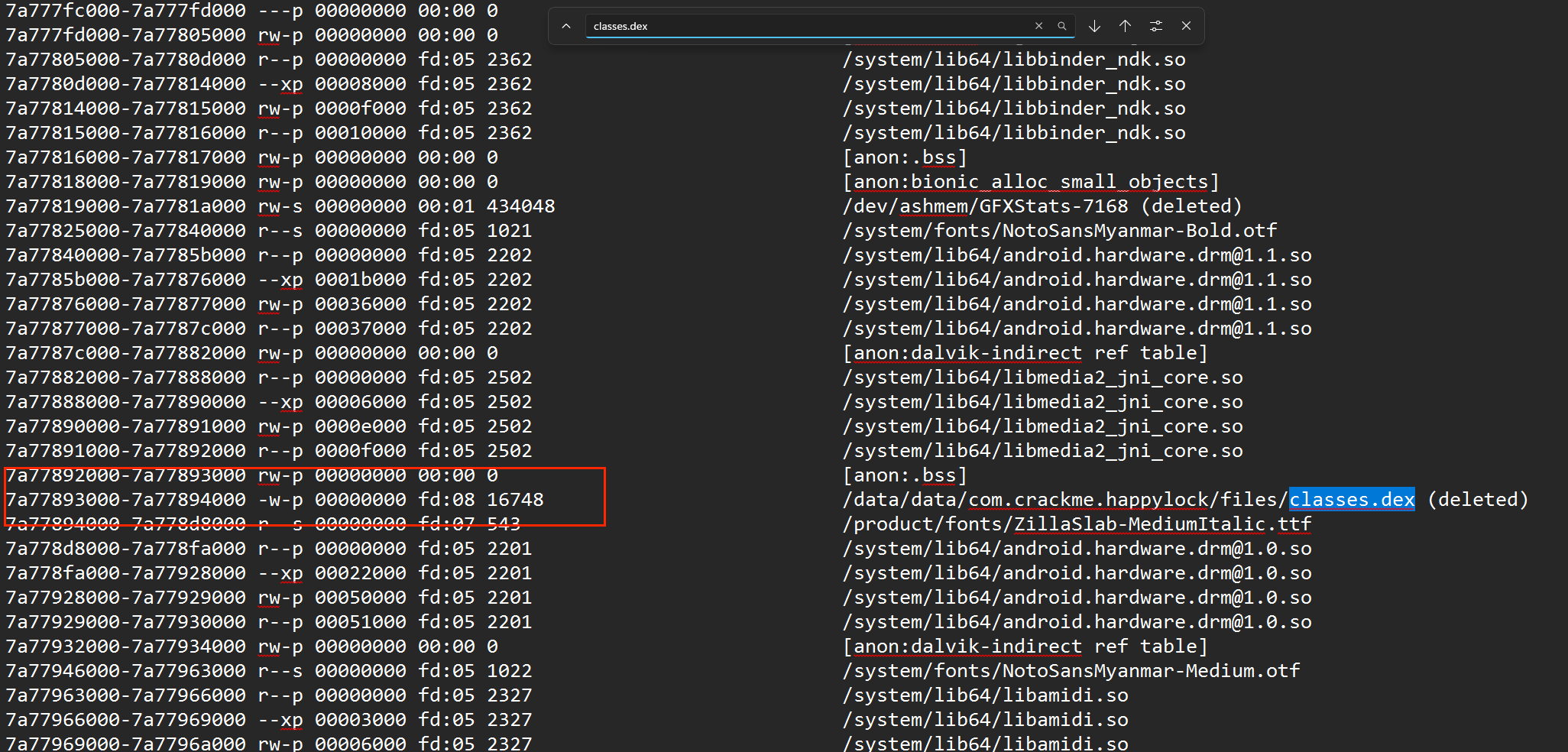
但我的安卓机好像是真断不上去啊,后面发现原因了,因为,他这个dex是加载完就会删的,所以得去jeb那里断在下面同调才行
具体方法懒得写,累….去问洋参
还有一种好玩的方法
1 2 https://blog.csdn.net/weixin_45582916?type=blog https://blog.csdn.net/qq_49619863/article/details/131155604
先
再
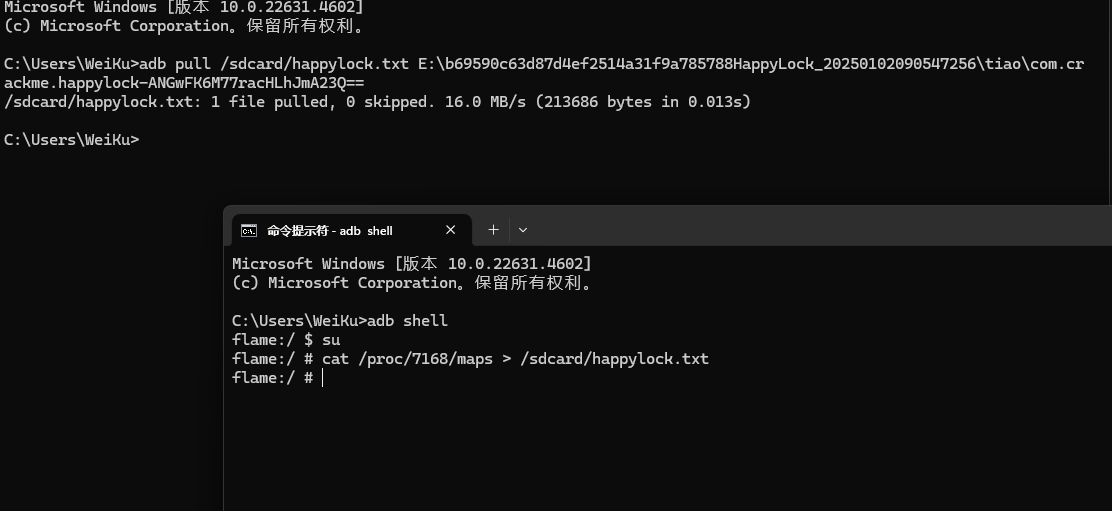
然后就是手机端操作,gg dump